Industrial companies worldwide are adopting capabilities that allow for remote operations. The pandemic has led companies to consider how they can reduce an onsite workforce while continuing with normal operations. Likewise, the worker shortage is leading companies to think in terms of a flexible workforce that may include remote staffing and flexible resourcing. In addition, industrials must think about emergency preparedness, control procedures, and the need to operate reliably with reduced onsite staff.
While the benefits to remote and mobile access are multifaceted, the risks to critical systems are real.
When workers and third-party vendors use remote communication technologies to directly access critical OT systems, the attack surface can be huge. A malicious actor can insert himself into the communication channel, overtake a legitimate user’s credentials, and utilize the data protocol such as RDP on the remote user’s device (i.e., a man in the middle attack) as a launching point to get into the OT network. The attacker can then move laterally to find vulnerable systems.
Quite obviously, this situation is completely untenable, and it is the scenario XONA Systems was created to solve. XONA prevents direct access to the network assets and includes multifactor authentication and an encrypted connection to mitigate the threat of man in the middle attacks on protected networks.
Remote Access Without Compromise of Essential Security
Operators need to provide remote and mobile workers with secure and managed access to operational controls as if they were there in person. This type of remote access absolutely requires a zero-trust architecture, control room managed access, and other operational safeguards. XONA’s Critical System Gateway (CSG) is purpose-built to fill this exact need.
XONA has a very simple architecture, shown below, that implements a zero-trust strategy to control, log and monitor the connection between the remote end user and the trusted asset in the OT network. As it relates to access, the questions of who, what, where, when, and why all are predetermined using a CSG appliance. Having this very well-defined architecture in place, companies with critical OT systems can now enable remote or mobile access without compromise of essential security.
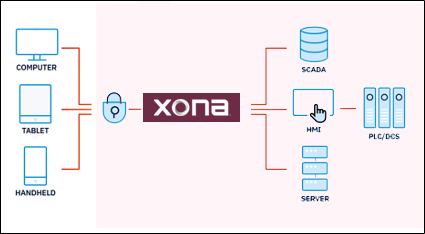
Here’s what it takes to implement this remote access solution.
On the user side:
A remote user can use a variety of device types. The device itself does not need to run any sort of software agent; however, it must be able to support the use of a physical key for multi-factor authentication (MFA). The user can connect via a virtual private network (VPN), but it isn’t necessary. The user can utilize any modern browser to gain access to the XONA CSG by directing the browser to a predetermined IP address, which connects into a specific port on the CSG.
On the OT side:
The target asset on the operational side can be anything that an operator would normally interact with—a SCADA system, PLCs, HMI servers, etc. These devices are defined, and a specific protocol is assigned and isolated by the XONA CSG appliance.
The XONA CSG:
The appliance has two ports—one to connect the user side and the other to connect the OT side. Once those connections are made, an administrator can configure the software to set up user accounts and profiles that determine who can access which assets (systems) or applications on the OT side, and when. These profiles are used to authenticate and authorize specific users or groups to each system.
In all, it can take as little as 30 minutes to install the XONA solution.
What XONA CSG Brings to Remote Access for OT Systems
CSG is the world’s first – and of course, best – zero-trust remote operations platform for critical infrastructure and other industrial facilities. XONA delivers a trusted solution with very unique features for a changing world.
Zero-Trust Architecture (ZTA) – First and foremost is XONA’s ZTA for access control. By definition, zero trust means that every entity, be it a person or a machine, inside or outside a network, must be authenticated, authorized, and continuously validated before gaining and maintaining access to a protected system, application, or data. The XONA platform adheres to the ZTA requirements outlined by NIST, which recommends a Policy Enforcement Point (PEP) for enabling, monitoring, and eventually terminating connections to a protected resource.
The XONA CSG provides this PEP between the IT and OT enterprise or for any connected assets. The CSG directly mitigates cyber risk and physical security gaps that are prevalent in the OT environment. These security features are extended to include any remote access to connected assets.
Multi-Factor Authentication (MFA) – MFA is required to connect a user’s device to the XONA CSG. The gateway allows entities to seamlessly authenticate with WebAuthn-, U2F-, or OTP-compliant hardware tokens. It can also integrate with a company’s legacy MFA solution.
Protocol Isolation – For those OT devices that communicate using any of three major protocols – RDP, VNC, or SSH – XONA is able to isolate those protocols to the OT network, so they are not utilized by the remote user on the untrusted user side. What the user interacts with are image files rather than the actual OT protocol, but they still have complete control of the OT device as if they were sitting in front of it. XONA uses proprietary technology to do this and is the only remote access company to have such a capability.
Agentless Access – For convenience, the XONA solution is clientless and browser-based, which means that the remote/mobile user can use any device without having to use plug-ins, agents, or client-based software. This kind of simplicity is especially important for third party access as well as emergency use situations where a user device doesn’t have to be pre-configured.
Logging and Recording – To help ensure security and compliance, XONA has user access logging, event logging, and screen recording of every action that is performed. These logs/recordings can be used for compliance purposes and for worker training.
Moderated Secure File Transfer – XONA provides the ability to send or receive files back and forth between the user and the OT asset. The file transfer can be configured to be bidirectional or unidirectional for a number of reasons, such as patching the asset or to pull log files from the asset. With moderated file transfer, the file is stopped at the CSG and an administrator must approve or deny the movement of the file from that point. It’s another layer of security checks and balances.
These and all other XONA features map to relevant NERC CIP controls and are compliant with other standards such as IEC 62443 and NIST 800-53.
In short, the XONA CSG is the ideal platform to serve as a simple and secure connection solution for secure remote or mobile plant operations.
Published February 11, 2022.
