Who’s Accessing Your Critical Systems and What Are They Doing?
Introduction
The ability to control and monitor who has access to critical systems is a fundamental pillar of cybersecurity. However, many organizations today struggle with fragmented identity management, leaving their operational technology (OT), industrial control systems (ICS), and/or cyber physical systems (CPS) environments vulnerable to security breaches, compliance violations, unnecessary business risks, and operational inefficiencies.
88% of analyzed industrial sites identified remote services (a MITRE ATT&CK® initial access vector) as their most significant cybersecurity risk.1
There is an urgent need to take control of user access across converged critical infrastructure (IT and OT) environments. The remote access solution market is seeing significant growth, driven by this increasing need and is growing at over 13% per year.
Industry analysts also recognize this urgent need. “Secure remote access provides critical infrastructure companies with a swift solution to address significant operational and business risks,” says Jonathon Gordon, Directing Analyst at Takepoint Research. “Mitigating these risks is a foundational step in strengthening the security of critical systems. Industrial enterprises should consider solutions specifically designed to address this security challenge for OT and IT teams.”
Today’s Lack of Unified Access Control
Legacy access solutions, such as VPNs, jump servers, and VDI, were not designed for the security and operational demands of today’s industrial environments. VPNs were introduced during President Clinton’s administration in the mid-1990s to provide privacy for traffic over the internet. These solutions create broad attack surfaces for critical systems because they provide open network connectivity for insecure endpoints to directly connect to critical systems. If a user endpoint is compromised, attackers can ‘ride’ the VPN tunnel directly into trusted customer networks exposing them to cyber-attack, ransomware and malware, credential theft, and lateral movement risks.
Further, these legacy remote access technologies are complex to manage, requiring constant patching and configuration, placing additional strain on overburdened IT, security, and operational teams. They also often fail to meet modern compliance standards, lacking the granular access controls and auditability needed to satisfy regulations like NERC-CIP and IEC 62443.
Legacy access solution limitations include:
- Designed for Privacy, Not Security – Legacy access solutions create an open hole in firewalls protecting critical systems and allow insecure user endpoints direct connectivity.
- Lack of User Access Control and Visibility – Traditional access solutions leave you in the dark with no understanding of who is accessing what in your environment. And there is little to no control or policy enforcement mechanisms to take that control back.
- Complex Configuration for Remote Endpoints – Third-party vendors and contractors often require endpoint agents or preconfigured devices, making remote access cumbersome and difficult to manage.
- No Support for Just-in-Time Access – Legacy systems often provide persistent access, increasing exposure to insider threats and credential misuse.
- Poor User and Admin Experience – VPNs and jump servers create friction for both users and administrators, requiring extensive setup and ongoing maintenance and patching.
- Scalability Challenges – As organizations expand, legacy access solutions become increasingly difficult to scale, leading to security gaps and operational inefficiencies.
The Importance of Access Control in Critical Infrastructure
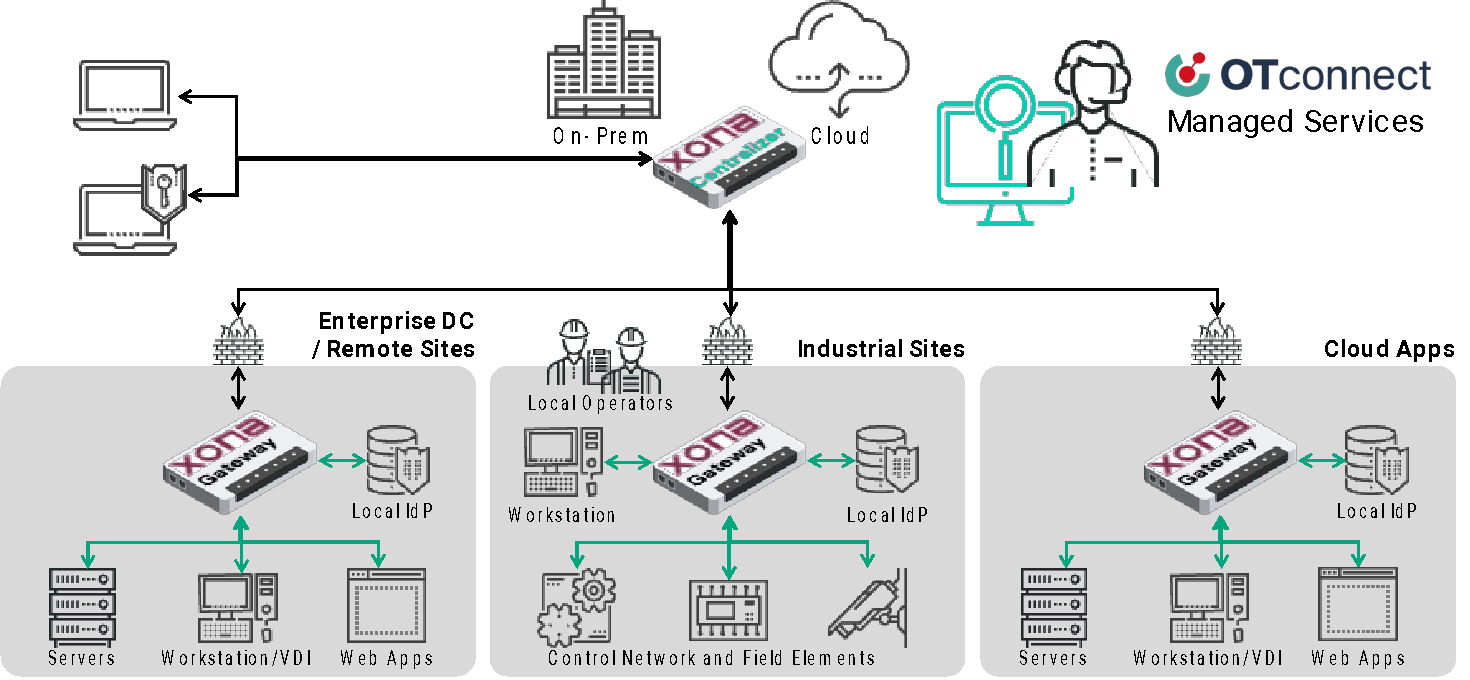
Modern industrial environments demand a security model that extends identity and access management (IAM) best practices into OT systems. A well-structured access control framework gives administrators complete control over who, what, when, where, and how users access critical systems. It provides granular identity, role-based, and attributed-based policy management controls. Secure access controls improve the security posture of critical systems reducing unauthorized access and mitigating the risk of insider threats. It improves operational efficiency streamlining user authentication processes and reducing administrative overhead. It increases scalability and flexibility enabling secure access management across diverse IT and OT ecosystems. And these solutions help ensure regulatory compliance aligning with security frameworks such as NERC CIP, IEC 62443, TSA security directives, NIS 2, CRA, NIST 800-53, Saudi NCA OTCC-1:2022, and others.
The Implications of Inadequate Access Control in Critical Infrastructure
Failing to implement a unified access control strategy can lead to significant security, business, and compliance risks. One example comes from a natural gas fired peaking power plant that struggled with fragmented access management. Due to inconsistent user authentication and lack of visibility into remote connections, unauthorized personnel were able to gain access to operational systems, creating a significant security threat. This lack of access control not only posed a serious cyber risk but also led to operational difficulties, requiring additional time and resources to manually verify and monitor access requests. Ultimately, these inefficiencies resulted in delays, increased costs, and compliance concerns related to NERC CIP regulations. By implementing a secure access management platform, the plant was able to centralize authentication, enforce role-based access policies, and gain real-time visibility into user activity. Read the full case study here.
Steps to Improve Secure Access for Critical Infrastructure
To mitigate these user access control challenges and associated risks, organizations should adopt a centralized and identity-based secure access strategy for their critical infrastructure. Key attributes of an effective approach that will help take back control of who is accessing what in your infrastructure include:
- Purpose Built for Critical Infrastructure – Next-generation access platform designed specifically for OT/ICS environments, users, and administrators; and supports typical onsite needs and low-bandwidth networks.
- Universal User Access Platform – Provides access control for internal employees, remote employees, 3rd party vendors, and OEM partners.
- Multi-Domain OT & IT Identity Integrations and Administration – Unifies identity administration across IT and local onsite OT identity stores. Supports existing AD, LDAP, SAML, MFA, IAM, and PAM systems.
- Standardized User Authorization, Authentication, and Policy Enforcement – Standardizes identity and multi-attribute policy management, authentication, and enforcement across converging IT-OT diverse deployments. Supports advanced MFA, SSO, adaptive and continuous authentication, device posture checks, and native authentication support for legacy OT/ICS elements.
- User Session Supervision, Collaboration, and Override – Provides the ability for one user or administrator to monitor another user’s session in real-time either through invitation or without. Enables session control override by administrators / production engineers. Provides users with the ability to share screens and pass controls to multiple team members.
Organizations that implement these best practices can significantly enhance their user access control, security, compliance, and operational efficiency.
Conclusion & Next Steps
Secure user access is a foundational element in critical infrastructure cybersecurity. Organizations that fail to take control of user access put their critical infrastructure at unnecessary risk to threats like ransomware and malware. The evolving threat landscape and increasing regulatory pressures demand a proactive approach to access management. By centralizing identity access, enforcing least privilege, and implementing continuous monitoring, companies can safeguard their OT environments against unauthorized access and cyber threats.
🔹 Evaluate your current access control policies.
🔹 Identify security gaps in your authentication framework.
🔹 Explore modern access control solutions designed for critical infrastructure.
Taking control of user access is no longer optional—it’s essential for ensuring the control, security, compliance, and resilience of critical operations.
Endnotes